In industries governed by the NIS2 Directive (Network and Information Systems Directive 2), ensuring secure and controlled access to critical computer systems is paramount. One of the most effective ways to achieve this is through NFC-enabled card readers combined with USB extenders, such as USB-Tec, featuring device class filtering. This powerful solution provides seamless user authentication, protects against unauthorized access, and ensures compliance with NIS2 requirements.
How the NFC Card Reader Access System Works
1. NFC Card for Secure Access
- Personalized Authentication: Each user is issued an NFC card linked to their credentials.
- Automatic Login: When a card is inserted into the NFC card reader, the system automatically logs the user into the terminal.
- Session Control: Removing the card immediately locks the terminal, ensuring no session remains open if the user steps away.
This eliminates the need for passwords, reducing vulnerabilities associated with weak or reused credentials, while streamlining the login process.
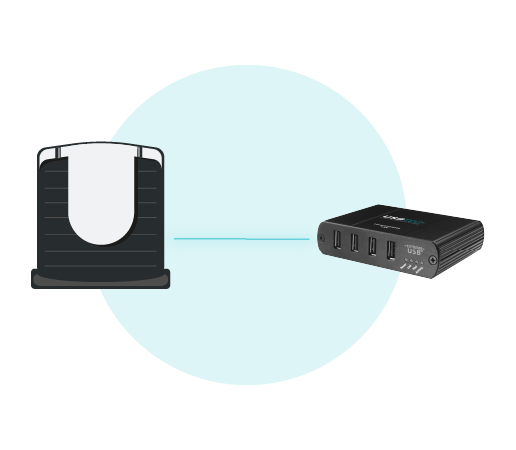
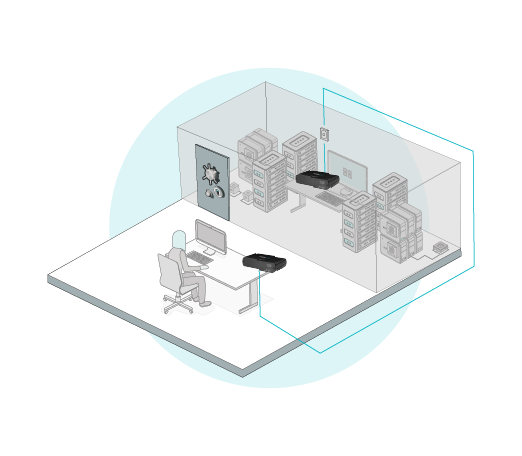
2. Air-Gapped Terminal Placement
To further secure sensitive systems, the computer terminal is kept in a separate, air-gapped room.
- Air-gapping physically isolates the terminal from external networks, reducing the risk of remote cyberattacks.
- The NFC card reader, keyboard, and mouse are connected to the air-gapped computer through a USB extender.
3. USB-Tec Extender with Device Class Filtering
USB-TEC extenders ensure that only authorized devices can interact with the computer terminal.
- Allowed Devices: The NFC card reader, keyboard, and mouse.
- Blocked Devices: Any unauthorized USB device, such as storage drives or other peripherals, are automatically rejected.
This setup prevents unauthorized users or devices from introducing malware or extracting data via USB connections, ensuring adherence to NIS2 standards for access control.

Benefits of NFC Card Reader Access
Strong Access Control
- Unique User Identification: Each NFC card is uniquely tied to an individual, ensuring only authorized personnel can log in.
- Zero Shared Credentials: Unlike shared passwords or accounts, NFC cards eliminate the risks associated with communal access methods.
- Immediate Locking: When the card is removed, the system locks instantly, preventing any unauthorized use of an unattended terminal.
This access model aligns perfectly with NIS2’s emphasis on user accountability and secure authentication mechanisms.
Simplified User Experience
- Fast and Efficient Login: No need to remember complex passwords—users simply insert their NFC card to gain access.
- Automated Logout: Removing the card secures the system with no additional steps required from the user.
This streamlined process not only improves user convenience but also ensures compliance with security protocols without introducing friction.
Protection Against Unauthorized Physical Access
With the computer terminal placed in an air-gapped room, the NFC card reader acts as the only physical access point. Combined with the USB extender’s device class filtering, this setup ensures:
- No external USB devices (e.g., flash drives) can be connected.
- Only verified peripherals, such as the card reader, keyboard, and mouse, are operational.
NIS2 Compliance Through NFC-Based Access Control
Access Control Policies
- NFC card-based authentication ensures only authorized users can access critical systems.
- Automated logging tracks access events for audit purposes.
Physical and Logical Security
- Placing the terminal in an air-gapped room isolates it from unauthorized access.
- Device class filtering limits connectivity to only approved peripherals.
User Accountability
- Individual NFC cards tie every action on the terminal to a specific user.
- Automatic session locking prevents misuse when users step away from the system.
Applications of NFC-Based Access Systems
Utilising NFC Card Readers and USB-Tec Extenders as a security access solution is particularly valuable in a wide range of industries. Some of the key industries where this solution helps the company in question adhere to NIS2 are:
Critical Infrastructure
Protecting control systems for utilities, manufacturing, and transport.

Healthcare
Securing terminals with sensitive patient records while enabling quick access for medical staff.

Finance
Ensuring only authorized personnel access sensitive financial data.
The combination of NFC card readers for secure access, USB-Tec extenders with device class filtering, and air-gapped terminal placement creates a powerful and secure environment that aligns with the NIS2 Directive. This setup enhances both security and user experience by ensuring robust access control while simplifying authentication procedures.
Organizations looking to bolster their cybersecurity posture and meet the highest regulatory standards should consider this streamlined, effective approach to system access and protection.

13 Comments
medicament kamagra pharmacie en ligne en france cheveux
donde comprar kamagra en mar del plata
commander kamagra en ligne sans ordonnance
enclomiphene fed ex cheap
order enclomiphene generic alternative
enclomiphene without prescription cod
androxal fedex without a perscription
purchase androxal cost uk
cheapest buy androxal buy online canada
compare dutasteride prices at major pharmacies
cheapest buy dutasteride purchase online canada
get dutasteride purchase line
ordering flexeril cyclobenzaprine uk cheapest
canadian drugstore online flexeril cyclobenzaprine
purchase flexeril cyclobenzaprine generic form
get gabapentin usa cheap
buy gabapentin usa pharmacy
gabapentin canada prescription
fildena without a prescription or doctor
discount fildena usa where to buy
discount fildena generic in canada
how to buy itraconazole canada shipping
buy cheap itraconazole purchase usa
is there a generic itraconazole avaliable in the usa
avodart no prescrption
discount avodart cheap alternatives
discount avodart generic mastercard
cheap staxyn us overnight delivery
online order staxyn cheap prescription
buying staxyn canada generic
order rifaximin cheap prescription
buy cheap rifaximin generic when will be available
discount rifaximin generic effectiveness
buy xifaxan cheap prescription
how to get a doctor to prescribe xifaxan
how to buy xifaxan cheap mastercard
kamagra bez předpisu fedex přes noc zdarma
kamagra cena v kanadě
koupit kamagra new york city